Friday’s Bybit hack was a darkish day for the crypto trade — and illustrates two issues.
For one, even exchanges with strong safety measures are susceptible to stylish assaults. And two, evolving ways imply North Korean hackers are an evolving risk, with their thefts getting bigger and extra frequent annually.
This was the most important hack within the historical past of crypto, with $1.4 billion gone within the blink of a watch — comfortably eclipsing the $625 million swiped from the Ronin Community virtually three years in the past.
Right here, Cryptonews will stroll you thru every little thing we all know concerning the assault thus far — together with what occurred, who was accountable, and the broader trade influence.
The Hack
Quickly after studies of the hack began swirling, Bybit launched a press release on X to substantiate that “unauthorized exercise” was detected in considered one of its ETH chilly wallets.
On the time, a routine switch was being made to a heat pockets, and the transaction had gone by a number of checks beforehand.
Bybit CEO Ben Zhou was the ultimate individual to log out — and after making a sequence of safety checks, he was happy that every little thing appeared so as. However though the proper vacation spot had been displayed for the switch, behind-the-scenes manipulation meant the funds have been really despatched to the hackers’ pockets.
Chainalysis says the preliminary compromise was through social engineering, and mentioned:
“The hackers gained entry to Bybit’s consumer interface by executing phishing assaults towards the chilly pockets signers, main them to signal malicious transactions that changed the Protected’s multi-signature pockets implementation contract with a malicious one.”
In a Areas dialog on X, Zhou revealed that he obtained a telephone name from his chief monetary officer half-hour after the transaction was accomplished.
“I can really feel one thing’s mistaken as a result of the man was simply shaking … he virtually can not converse. ‘Ben, there was a problem … we may be hacked.'”
The CEO mentioned he initially thought that 30,000 ETH — price about $82 million — was affected, however was then instructed that 401,000 ETH had been saved on this chilly pockets. All of it was gone.
“I had this overwhelming breathlessness, I couldn’t breathe. For about 5 seconds I didn’t say something. I take into consideration 10 seconds later I instructed myself that I wanted to snap out of it.”
Zhou mentioned he enacted fast safety protocols that had been rehearsed as soon as a month — and he used a button enabling him to get up everybody within the firm, in addition to prime administration. At that time, the manager says his prime precedence wasn’t to recoup the $1.4 billion — however to guard Bybit’s status.
A livestream was unexpectedly organized so Zhou may reply questions from Bybit clients, however there have been two issues he wished to emphasize to clients: all different chilly wallets have been fantastic, and the trade was capable of cowl the loss as a result of buyer property are backed on a one-to-one foundation.
Earlier than that broadcast started, Zhou wrote a message to workers that mentioned:
“Pricey Bybuddies, perceive that it’s a tough time now. I recognize that every one of you stand in line. It’s going to be a tough 24 to 48 hours that we are going to face, however I’m assured that we are going to make it by. Please guarantee we stay skilled and calm to all purchasers and exterior companions. We are going to strive our greatest to stay withdrawals. On the identical time, I wish to say even with this quantity of loss, all consumer property are lined. It’s the time to reply purchasers’ questions in a well timed method, and be there with our purchasers, and we are going to use transparency and communication to take away doubts from our purchasers.”
Zhou precisely foresaw what was coming — and finally, it appears Bybit managed to return good on that promise. The trade later revealed that it had processed a staggering 350,000 withdrawal requests throughout the first 10 hours of the hack… and 580,000 had efficiently been accomplished by Saturday. As soon as that backlog was cleared, the corporate mentioned all of its techniques have been working usually.
Sustaining that aura of “enterprise as typical” mattered, as many buying and selling platforms have all of a sudden halted withdrawals prior to now — and within the case of FTX, this was the precursor to a protracted and messy chapter.
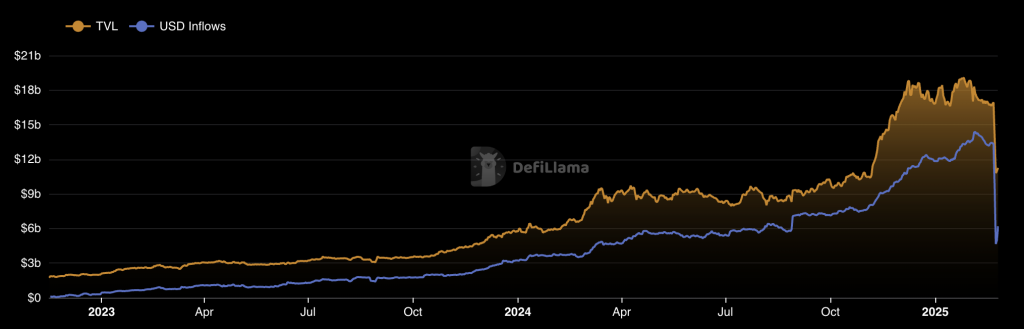
DeFiLlama knowledge exhibits Bybit had near $17 billion in complete property earlier than the hack came about, however this had plunged to $10.8 billion by Sunday as clients raced to drag funds out of their accounts. As of Tuesday, that determine had rebounded barely — nudging as much as $11.5 billion.
The Hackers
As Bybit raced to calm clients and the markets, on-chain investigators have been attending to work too — and discovering out who was accountable.
Inside hours of the $1.4 billion hack going down, ZachXBT had uncovered definitive proof that the Lazarus Group was behind this exploit.
It is a collective that has shut ties to the North Korean authorities, with U.S. officers claiming that stolen crypto finally ends up being laundered, cashed out, and used to fund the remoted state’s applications to construct ballistic missiles and weapons of mass destruction.
The Lazarus Group’s fingerprints have been on among the greatest hacks to rock the crypto trade lately — together with the $234 million WazirX theft earlier this yr, the $100 million stolen from each Atomic Pockets and Horizon, and that jaw-dropping $625 million swiped from the Ronin Community.
Whereas crypto transactions are traceable to an extent, mixers and decentralized exchanges permit these cybercriminals to obfuscate the supply of funds, making it seem to be they’re gone and not using a hint. Wanting on the Lazarus playbook following the Ronin assault, Chainalysis senior director of investigations Erin Plante mentioned:
“They transfer the funds actually rapidly they usually transfer them by lots of various kinds of obfuscation to get to some extent the place they will attempt to rapidly money out. They hope investigations are a number of phases behind as a result of they’re solely going to maintain the funds in a freezable state — like a stablecoin or a centralized trade — for 5 or ten minutes. They usually hope that they’ve gotten simply far sufficient forward of investigators, and put simply sufficient laundering in there, that the companies aren’t going to know the place they observe again to.”
Arkham Intelligence has been monitoring what’s occurring to the 401,000 ETH stolen from Bybit — mapping out a constellation of wallets the place the crypto has been distributed thus far. It wrote:
“The Bybit Hacker is making 2-3 transactions per minute, and stops each 45 minutes for a 15 minute break. They transfer ETH from one deal with at a time, earlier than shifting onto the following one.”
Up to now, it appears the Lazarus Group has been swapping this stolen Ether primarily for Bitcoin, in addition to the DAI stablecoin. Decentralized exchanges, cross-chain bridges and prompt swap companies that don’t implement Know Your Buyer checks have been relied on to move funds throughout blockchains.
However after all, $1.4 billion is some huge cash — and Chainalysis has warned that the hackers gained’t be afraid to let a few of this crypto lay dormant for a short time.
“By delaying laundering efforts, they goal to outlast the heightened scrutiny that sometimes instantly follows such high-profile breaches.”
BYBIT HACKER LAUNDERING FUNDS
The Bybit Hacker is making 2-3 transactions per minute, and stops each 45 minutes for a 15 minute break. They transfer ETH from one deal with at a time, earlier than shifting onto the following one.
Did Lazarus get an intern to scrub their funds manually? pic.twitter.com/XCS16hMC3i— Arkham (@arkham) February 24, 2025
The Fightback
Bybit has now launched a bounty program that’s designed to reward safety specialists who assist recuperate this stolen crypto — which means they’ll obtain 10% of any funds recovered. Meaning there’s as much as $140 million up for grabs.
However progress has been fairly restricted thus far. By Sunday, solely $85 million of the funds taken by Lazarus Group had been frozen or recovered… amounting to barely 5% of what’s lacking.
On Monday, the trade claimed that it has additionally managed to totally shut the ETH hole of consumer property inside 72 hours — including “strategic partnerships with corporations like Galaxy Digital, FalconX and Wintermute, together with help from Bitget, MEXC and DWF Labs, helped Bybit replenish the reserves in document time.”
This was bolstered by a Hacken audit that confirmed the crypto platform — which is the world’s second largest when it comes to buying and selling volumes — “possesses ample reserves to cowl consumer property 1:1 throughout the board.”
Bybit had launched Proof of Reserves in direct response to the FTX hack — and on the time, mentioned “laying every little thing on the desk deters a crypto trade from making secretive monetary transactions.”
Zhou was requested on X whether or not he believes that there’s any likelihood his trade will get this stolen crypto again — and if there’s any level in getting legislation enforcement companies concerned. He mentioned:
“We are going to strive our greatest … I assume it’s going to take a protracted, very long time for the hackers to scrub this cash out. We hope that by including sufficient hassle for them, perhaps they’d think about returning it in some unspecified time in the future … the Singapore police took it significantly and have already escalated it to Interpol stage.”
By the seems to be of issues thus far, any likelihood of the Lazarus Group realizing the error of their methods and sending the crypto again seems to be exceedingly unlikely.
The Risk
Chainalysis has lengthy been conserving tabs on the Lazarus Group, and it’s clear to see their hacks on crypto exchanges are escalating.
North Korea was chargeable for about two-thirds of the funds stolen from this trade in 2024 — however this doesn’t inform the entire story.
Roughly $660 million was stolen by Lazarus throughout 20 incidents in 2023, surging to $1.34 billion in 47 hacks final yr. Simply two months into 2025, this group has managed to interrupt information — and that was by only one assault.
Consideration is now turning as to whether such assaults may be prevented sooner or later — and whether or not crypto exchanges are a protected surroundings for traders to retailer their property.
Ledger CEO Pascal Gauthier has argued that buying and selling platforms must rethink their safety measures altogether, and make a concerted shift to new approaches corresponding to “Clear Signing.” On X, he wrote:
“Safety isn’t static — attackers are getting smarter, and our trade should keep forward by implementing the very best enterprise safety requirements to forestall the following, extra subtle assault.”
Clear Signing implies that particulars a few transaction are offered in a human-readable format, and Gauthier argues that Bybit’s exploit wouldn’t have occurred had this safety layer been applied.
Ledger has additionally confused that this newest hack underline the necessity for self-custody — and customers must be counting on {hardware} wallets as an alternative of entrusting their funds with exchanges.
The submit The Bybit Hack Defined: What Occurred, Who Did It, What Occurs Subsequent appeared first on Cryptonews.
