A safety breach tied to decentralized change aggregator Matcha Meta has resulted within the theft of roughly $16.8 million in crypto belongings, including to a rising record of smart-contract exploits that proceed to check the security assumptions of DeFi customers.
The incident unfolded on Sunday and was traced to not Matcha’s core infrastructure, however to SwapNet, one of many liquidity suppliers built-in into the platform.
Matcha Meta disclosed the difficulty publicly in a submit on X, saying customers who had disabled its “One-Time Approval” characteristic and as an alternative granted direct token allowances to particular person aggregator contracts might have been uncovered.
We’re conscious of an incident with SwapNet that customers might have been uncovered to on Matcha Meta for many who turned off One-Time Approvals
We’re involved with the SwapNet staff they usually have briefly disabled their contracts
The staff is actively investigating and can present…— Matcha Meta
(@matchametaxyz) January 25, 2026
The protocol urged affected customers to instantly revoke approvals linked to SwapNet’s router contract, warning that failure to take action might depart wallets susceptible to additional unauthorized transfers.
$17M Vanishes in Seconds: How Matcha Hackers Slipped Funds Onto Ethereum
Blockchain safety companies rapidly started monitoring the exploit as funds moved on-chain.
PeckShield reported that roughly $16.8 million had been drained in complete, with the attacker swapping round $10.5 million in USDC for roughly 3,655 ETH on the Base community earlier than beginning to bridge belongings to Ethereum.
#PeckShieldAlert Matcha Meta has reported a safety breach involving SwapNet. Customers who opted out of "One-Time Approvals" are in danger.
Thus far, ~$16.8M price of crypto has been drained.
On #Base, the attacker swapped ~10.5M $USDC for ~3,655 $ETH and has begun bridging funds to… https://t.co/QOyV4IU3P3 pic.twitter.com/6OOJd9cvyF— PeckShieldAlert (@PeckShieldAlert) January 26, 2026
CertiK independently flagged suspicious transactions, figuring out one pockets that siphoned about $13.3 million in USDC on Base and transformed the funds into wrapped Ether.
Each companies pointed to a vulnerability within the SwapNet contract that allowed arbitrary calls, enabling the attacker to switch tokens that customers had beforehand accredited.
1/ The vulnerability appears to be in arbitrary name in @0xswapnet contract that permit attacker to switch funds accredited to it. (https://t.co/B7ux5zzMLS)
The staff have briefly disabled their contracts is actively investigating.https://t.co/NBNvzxHCRw
Please revoke approval…— CertiK Alert (@CertiKAlert) January 26, 2026
Matcha later clarified that the incident was not linked to 0x’s AllowanceHolder or Settler contracts, which underpin its One-Time Approval system.
The staff famous that customers who interacted with Matcha utilizing One-Time Approvals weren’t affected, as this design limits how a lot entry a third-party contract can retain.
After reviewing with 0x's protocol staff, we’ve confirmed that the character of the incident was not related to 0x's AllowanceHolder or Settler contracts.
Customers who’ve interacted with Matcha Meta through One-Time Approval are thus secure.
Customers who’ve disabled One-Time… https://t.co/VQVmj4LL0F— Matcha Meta
(@matchametaxyz) January 25, 2026
The publicity, the staff mentioned, utilized solely to customers who opted out of that system and granted ongoing allowances on to aggregator contracts. In response, Matcha has eliminated the choice for customers to set such direct approvals going ahead.
Outdated Token Approvals Emerge as a Persistent DeFi Weak Spot
The breach highlights a recurring pressure in DeFi between flexibility and security. Token approvals, whereas needed for interacting with good contracts, have lengthy been a weak level, notably when permissions stay lively lengthy after a transaction is accomplished.
On this case, beforehand granted allowances grew to become the pathway for the exploit as soon as the SwapNet contract was compromised.
The incident arrives amid continued issues over smart-contract safety throughout the crypto sector.
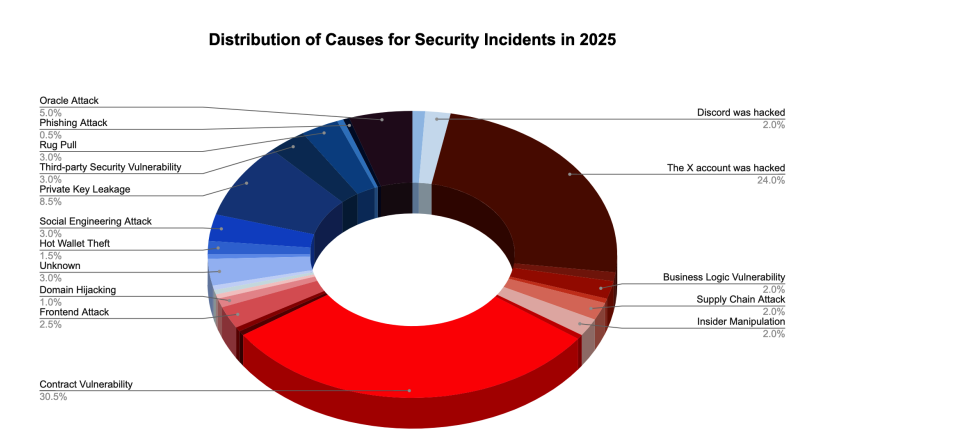
SlowMist’s year-end report reveals that vulnerabilities in good contracts accounted for simply over 30% of crypto exploits in 2025, making them the main reason for losses.
Researchers have additionally warned that advances in synthetic intelligence are accelerating how rapidly attackers can establish and exploit weaknesses in on-chain code.
Whereas general crypto losses declined in December, falling about 60% month-on-month to roughly $76 million, safety companies cautioned that the drop didn’t mirror a structural enchancment.
Crypto-related losses from hacks and cybersecurity exploits fell sharply in December, dropping 60% month-on-month to about $76 million.#Crypto #Hackhttps://t.co/mke6K8sLVQ
— Cryptonews.com (@cryptonews) January 2, 2026
PeckShield famous {that a} single address-poisoning rip-off accounted for $50 million of December’s losses, exhibiting how concentrated and extreme particular person incidents might be even throughout quieter intervals.
January has already seen a number of notable exploits. IPOR Labs confirmed a $336,000 assault on its USDC Fusion Optimizer vault on Arbitrum, whereas Truebit disclosed a smart-contract incident that on-chain analysts estimate drained greater than 8,500 ETH, triggering a near-total collapse within the challenge’s token value.
Final week, Layer-1 community Saga paused its SagaEVM chain after an exploit moved near $7 million in belongings to Ethereum.
The submit Matcha Meta Breach Drains $16.8M through SwapNet Exploit — Customers Urged to Revoke Entry appeared first on Cryptonews.
