Key Takeaways:
- Procolored’s official driver downloads contained XRedRAT (a distant entry trojan) and SnipVex (a Bitcoin clipboard hijacker).
- The malware, linked from Procolored’s personal assist website, swapped copied Bitcoin addresses to redirect funds to attackers, netting round 9.3 BTC.
- After public publicity, Procolored’s father or mother firm, Tiansheng, eliminated the contaminated recordsdata, blaming the breach on USB cross-contamination.
Chinese language printer producer Procolored has been discovered distributing malware by way of its official printer drivers, exposing customers to severe cybersecurity dangers. The malicious software program, which included a distant entry trojan and a cryptocurrency stealer, seems to have been embedded in Procolored’s companion software program for a minimum of six months.
Procolored, primarily based in Shenzhen, China, focuses on digital printing options equivalent to DTF, UV, and DTG printers.
Since its founding in 2018, the corporate has expanded quickly, promoting in over 30 nations, together with the U.S., the place it has a giant buyer base.
Malware Present in Procolored Printer Software program, Impacting Customers Globally
In accordance with native information media, the problem got here to mild when YouTuber Cameron Coward, often called Serial Hobbyism, detected malware on his system after putting in drivers for a $7,000 Procolored UV printer. His antivirus flagged a worm often called Floxif.
Coward initially contacted the corporate, which denied any wrongdoing and claimed the alert was a false constructive. “If I attempt to obtain the recordsdata from their web site or unzip the recordsdata on the USB drive they gave me, my pc instantly quarantines them,” Coward stated.
Looking for readability, Coward turned to Reddit for assist. That led to a deeper investigation by Karsten Hahn, a researcher at cybersecurity agency G Information.
Hahn confirmed the presence of two items of malware: XRedRAT, a distant entry trojan able to keystroke logging and distant management, and SnipVex, a beforehand unknown clipboard hijacker focusing on Bitcoin addresses.
The malware was traced to a minimum of six Procolored printer fashions, with contaminated recordsdata hosted on Mega, linked immediately from Procolored’s official assist website. A complete of 39 compromised recordsdata had been discovered.
The malware changed copied Bitcoin pockets addresses with ones managed by attackers, stealing funds from unsuspecting customers.
A complete of 9.3 BTC price over $953,000 has been stolen, in line with the report. Crypto monitoring and compliance agency Sluggish Mist described how the malware operates in a Might 19 X put up:
“The official driver supplied by this printer carries a backdoor program. It should hijack the pockets handle within the person’s clipboard and substitute it with the attacker’s handle.“
The official driver supplied by this printer carries a backdoor program. It should hijack the pockets handle within the person's clipboard and substitute it with the attacker's handle: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
In accordance with @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
— MistTrack
(@MistTrack_io) Might 19, 2025
G Information contacted Tiansheng, the father or mother firm of Procolored. The agency responded that it had eliminated the affected drivers and rescanned all recordsdata as of Might 8, 2025.
The corporate claimed the an infection possible occurred throughout USB transfers between techniques earlier than the recordsdata had been uploaded on-line.
Customers are actually urged to scan their techniques completely. Consultants suggest a full system reinstall for anybody who has used the contaminated drivers. New, clear driver recordsdata are reportedly accessible however have to be requested immediately from Tiansheng’s technical assist.
Chinese language Marketplaces and US Fronts Gasoline Southeast Asian Fraud Rings
The invention of Bitcoin-stealing malware in Procolored’s official printer drivers comes amid a wider wave of cybercrime infrastructure originating in China and spreading throughout Southeast Asia.
On Might 18, blockchain agency Elliptic linked a Colorado-incorporated entity to a Chinese language-language Telegram market referred to as Xinbi Assure, a platform used to facilitate large-scale crypto scams.
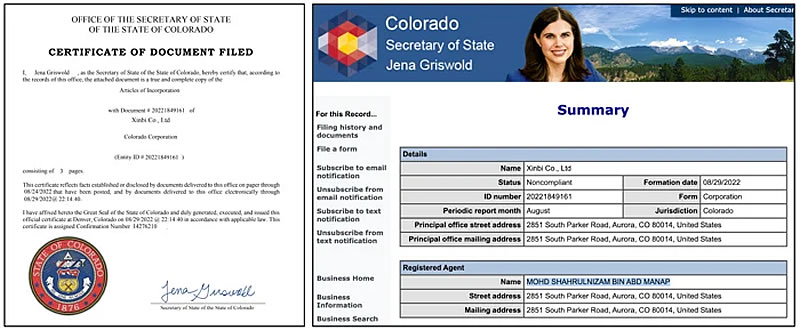
Xinbi has processed over $8.4 billion in stablecoin transactions, primarily USDT, since its inception. The platform affords illicit companies starting from cash laundering and faux IDs to tech {hardware} and stolen private information.
It operates on a “assure” mannequin, requiring vendor deposits to take care of belief amongst criminals.
Xinbi was registered within the U.S. in 2022 underneath the title Xinbi Co. Ltd. The corporate was flagged as delinquent in early 2025 for failing to file studies. Elliptic suggests the group’s crypto exercise might also be tied to North Korean hackers.
Xinbi follows Huione Assure, one other Chinese language market uncovered in 2024 for facilitating $98 billion in transactions.
These networks reveal a rising underground financial system powered by stablecoins and an alarming rise in cyber fraud.
The put up Procolored Printer Drivers Slip Bitcoin-Stealing Trojan, Draining $950K from Customers appeared first on Cryptonews.
